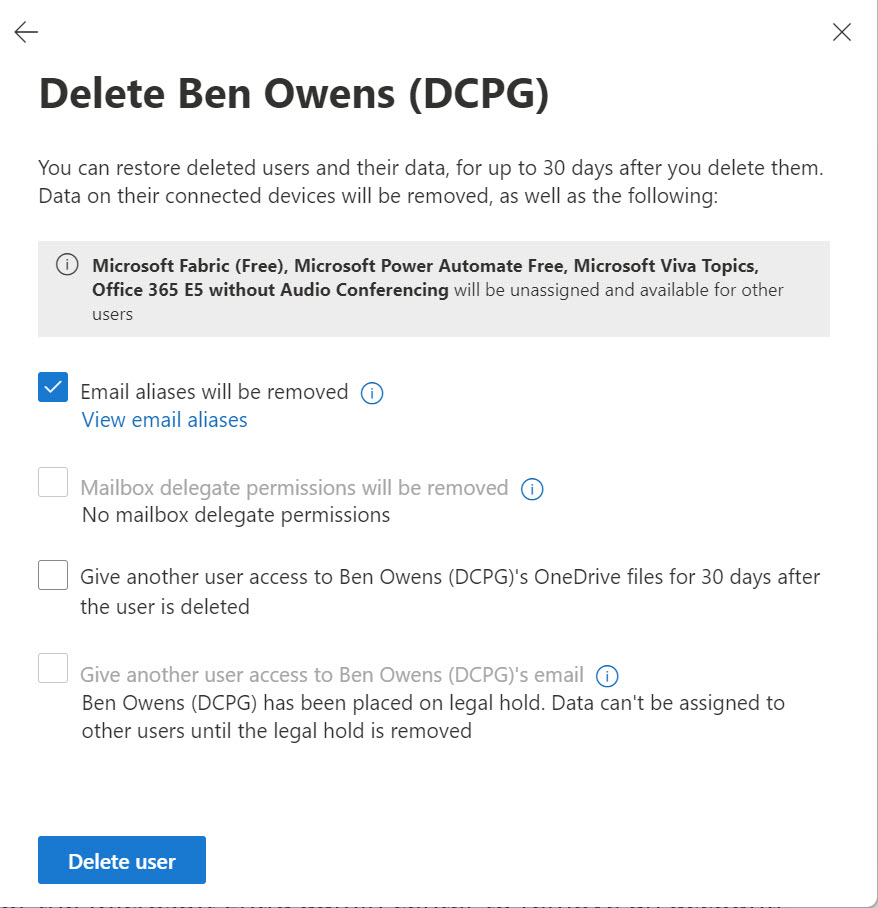
Enterprise apps can come from a variety of sources. Most are Microsoft 1st party apps, and the rest are ISV apps. It’s easy to add an app without really intending to, which is a good reason to force users through the Entra ID app consent workflow when they want to add an app. Unhappily, I failed the test and added an app in a moment of weakness. Here’s what happened.
The Entra ID password protection policy contains settings that affect how tenants deal with passwords. Entra ID includes a default policy that doesn’t require additional licenses. Creating a custom password protection policy requires tenant users to have Entra P1 licenses. As explained in this article, once the licensing issue is solved, it’s easy to update the policy settings with PowerShell.
Entra ID is about to introduce passkey profiles, a more granular approach to passkey settings. The change is good, but you might like to check the current passkey settings to make sure that the values inherited by the new default passkey profile behave the way that you want. In particular, check attestation enforcement to make sure that the right kind of passkeys are used.
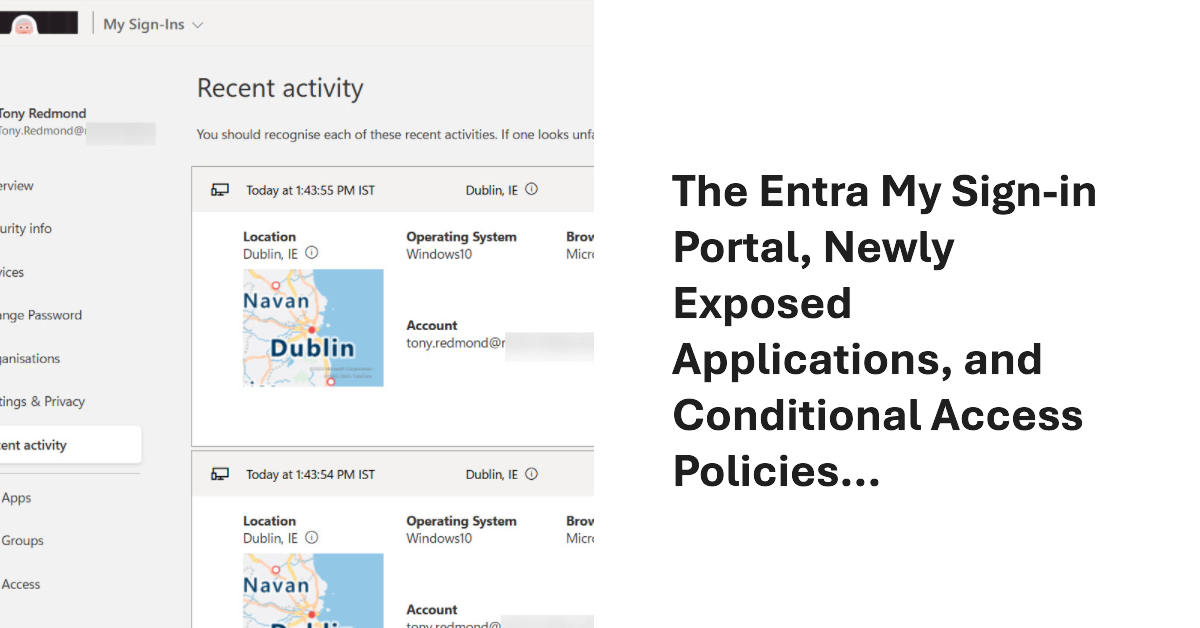
A recent change has exposed the applications used by the My Sign-ins portal for use in conditional access policies. This article discusses the app-centric nature of Microsoft 365 and Entra ID and why it’s important that the newly-revealed set of applications are available for conditional access processing, just in case the Entra ID agents planned by Microsoft can’t optimize your policies.
New Graph APIs allow Entra administrators to restore a conditional access policy with a Graph request. This article explains how to list, restore, and permanently remove soft-deleted conditional access policies using Graph API requests run in PowerShell. Being able to restore conditional access policies removed in error closes a big gap, especially if agents might begin working on policies. Who knows what errors might happen in future.
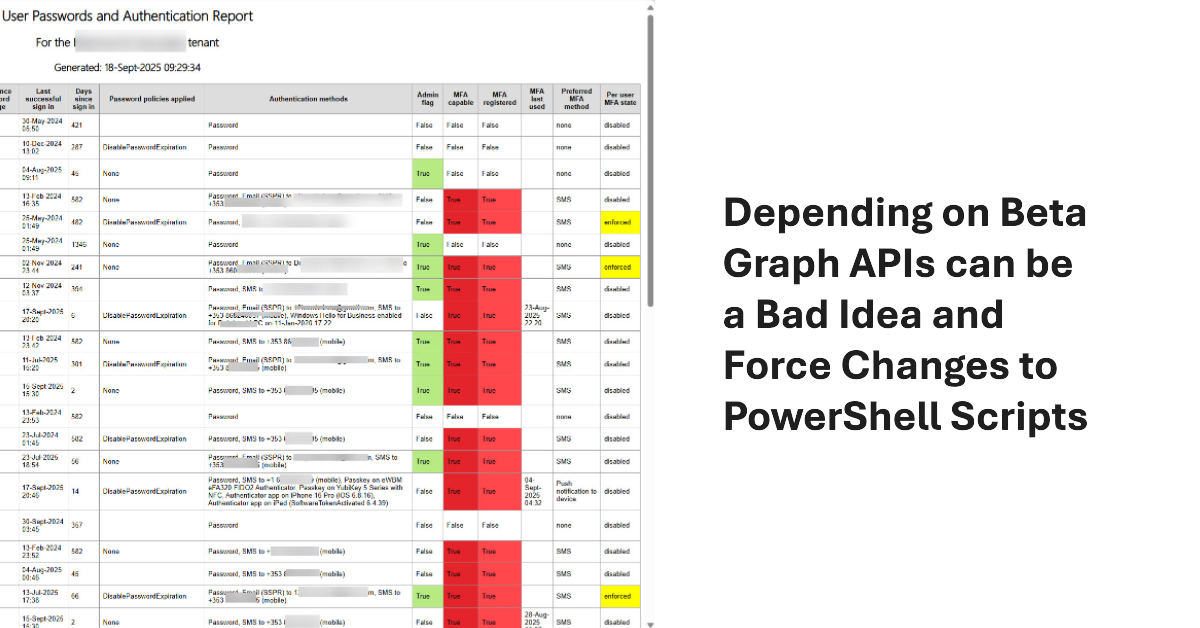
A change to a Graph beta API meant that some data used to create the user password and authentication report was no longer available. A script update was required. The experience underlines the truth that developers should not rely on the Graph beta APIs because the APIs are prone to change at any time as Microsoft moves them along to become production-ready.
Guest account management should be a part of every Microsoft 365 tenant administrator’s checklist, unless the tenant has no guests. That’s possible but given the way that workloads like Teams and SharePoint Online create new guest accounts, the average tenant is likely to have quite a few guests. The question is how to manage guests – with Microsoft’s tools or using tenant-designed PowerShell scripts?
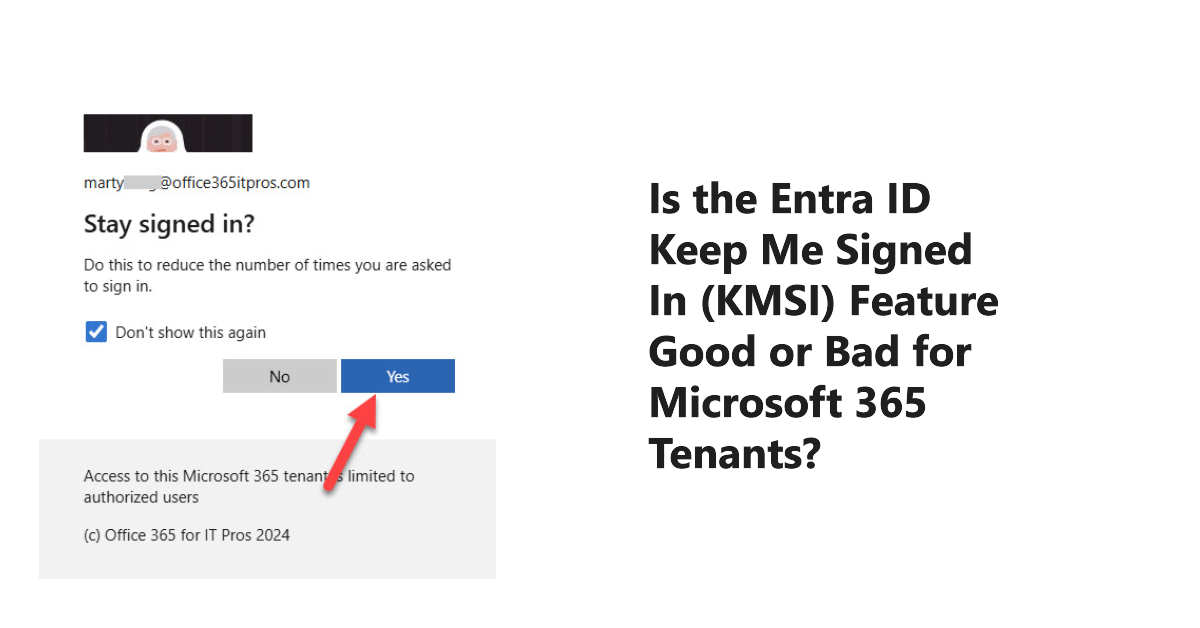
The Entra ID Keep Me Signed In (KMSI) feature creates persistent authentication cookies to allow users to avoid sign-ins during browser sessions. Is this a good or bad thing and should Microsoft 365 tenants enable or disable KMSI. I think KMSI is fine in certain conditions and explain my logic in this article. Feel free to disagree!
The Org Settings section of the Microsoft 365 admin center has a new People Settings section where you can choose properties for the Microsoft 365 profile card instead of using PowerShell. The kicker is that the old method of using Exchange custom properties to customize what appears on the profile card is being replaced with standard Entra ID properties. A migration is needed, and it’s easily done with PowerShell.
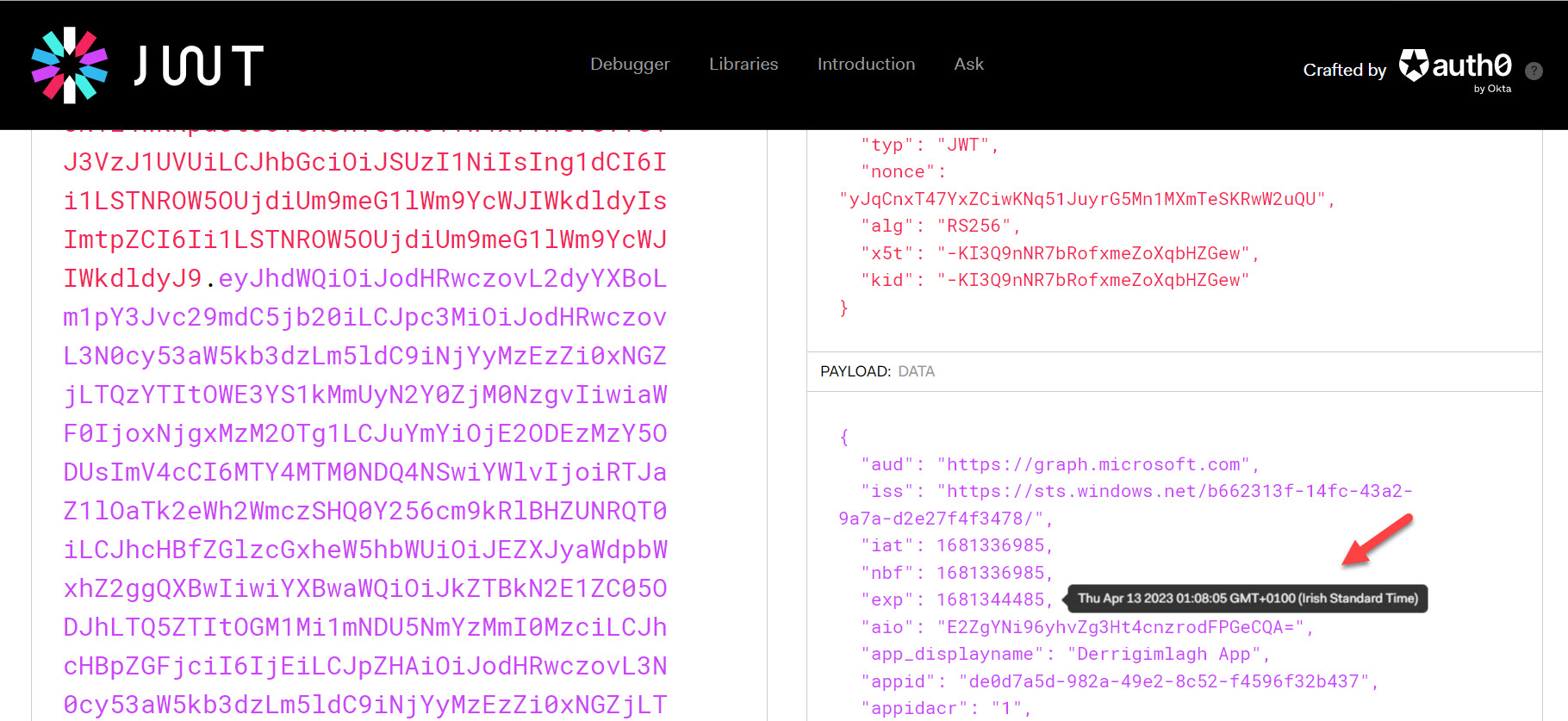
Three new Graph API resources provide easy access to Entra ID authentication method summary data. The information is helpful to understand the type of sign-ins that happen, and the authentication methods used by user connections. The article includes a script based on the MFA sign-in summary to highlight non-MFA connections and the apps users connect to.
A banner posted in the Entra admin center informs administrators that Entra ID governance features used by guest accounts incur charges from June 2025. This only affects Microsoft 365 tenants that use ID governance for features like inactive guest access reviews, but unexpected charges might come as a surprise. This article explains a PowerShell script to find chargeable events in audit logs and how to calculate likely charges.
Linkable token identifiers is a new Entra ID feature that adds a GUID to all the audit events for a session. The new identifiers make it easier to track all user actions taken during a session, and should be of great advantage to security investigators who need to know if an account is performing suspicious actions, possibly due to an attacker compromise.
The conditional access policy condition for token protection now extends to Microsoft Graph PowerShell SDK interactive sessions. Any account within the scope of a CA policy that requires token protection can use Web Account Manager (WAM) to sign in and check that everything is secure and ready to go. It’s a protection that might be of interest to administrators and developers that access sensitive data in Graph SDK sessions.
In July, Microsoft plans to introduce an app consent policy to stop users granting access to third-party apps to their files and sites. Letting users grant unsupervised consent to third-party apps to access files stored in OneDrive for Business and SharePoint Online is a bad idea. There are certainly apps out there that need such access, but requiring one-time administrator approval is no hardship.
Microsoft 365 tenants with Entra P1 or P2 licenses can use a custom banned password list to stop people using specific terms in their passwords. The idea is to prevent easily-guessed terms being used in passwords. You could also block words deemed to be objectionable. In any case, this article explains how to maintain the custom blocked password list with a PowerShell script.
After July 1, 2025, any sharing links generated with one-time passcodes (OTP) will stop working. Only links based on Entra ID B2B Collaboration will work. Users who lose access to content shared from SharePoint Online or OneDrive for Business will have to contact the original sharer to ask them to generate a new sharing link. Sounds like a recipe for confusion, which is what might happen.
The prospect of agents running amok in Microsoft 365 tenants lessened a tad with the introduction of Entra Agent ID. Tenants will be able to manage agents through the Entra admin center. Custom agents created with Copilot Studio or Azure AI Foundry now have Entra identifiers and show up in the admin center. So far, not much else happens but the promise of more functionality is there.
The ConditionalAccessPolicy setting in an OWA mailbox policy can be configured to work with Entra ID conditional access so that OWA blocks access to attachments on unmanaged devices. Microsoft originally introduced the feature in 2018 and as it turns out, the combination of OWA mailbox policy and CA policy also blocks attachment access for the new Outlook for Windows client.
Microsoft will disable service principal-less authentication in March 2026. This step closes a hole that doesn’t exist today but might in the future. The strange thing is that many Microsoft 365 applications seem to use service principal-less authentication. Microsoft will take care of first-party apps before March 2026, but there’s work to do for apps from other vendors.
The Conditional Access Optimization Agent is one of 6 Security Copilot agents unveiled by Microsoft on March 24, 2025. The idea is that the agent can optimize CA policies by observing the connectivity behavior within a tenant. The agent can suggest how to fill gaps in CA coverage, detect new users and apps, and generally be helpful. Is it worth it? Experience will tell…
The February 2025 EX1015484 incident explains why mail user objects with duplicate SMTP addresses are created for guest accounts. That’s a problem because Exchange Online can’t route messages to objects with duplicate email addresses. Fortunately, you can find out if any duplicates exist in your tenant with some PowerShell. Problems happen!
A new preview option in the Entra admin center supports the ability to update multiple Entra ID accounts. You can update properties, add managers and sponsors, update group membership, revoke account access, and so on. The only surprising thing about the new option is that it’s taken Microsoft so long to add it to the admin center.
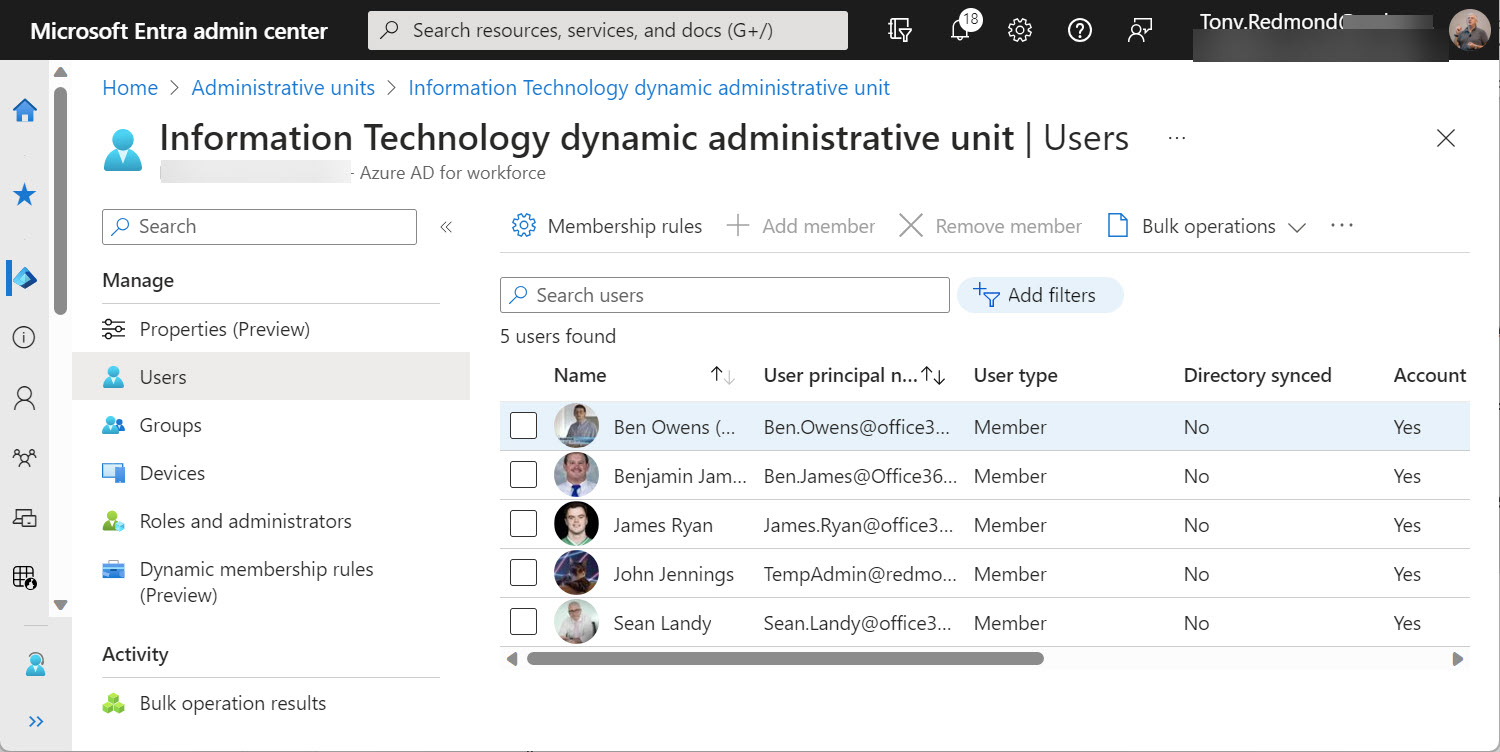
A reader asked how they could create dynamic administrative units for every department in their directory. A PowerShell script does the job, even if some constraints in how Entra ID processes membership rules means that the rules can’t be quite as precise as I would like them to be.
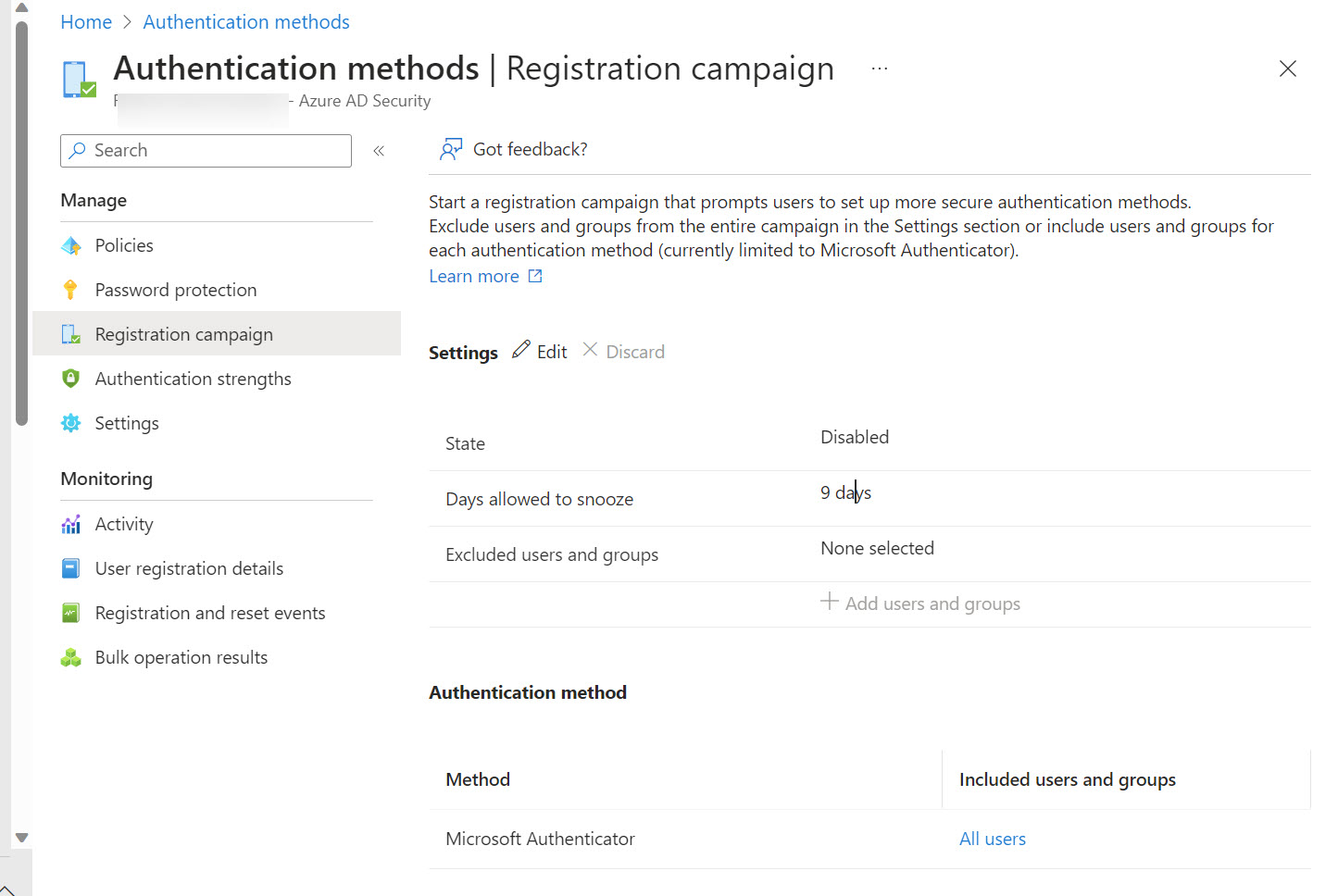
Entra ID includes a registration campaign feature to help organizations move users to stronger authentication methods like the Authenticator app. Running campaigns is a good thing, unless you decide to do it when the administrators are away from the office (like me) or users are unprepared. But it is time to get rid of SMS and voice responses to MFA challenges, so maybe you should schedule a campaign soon?
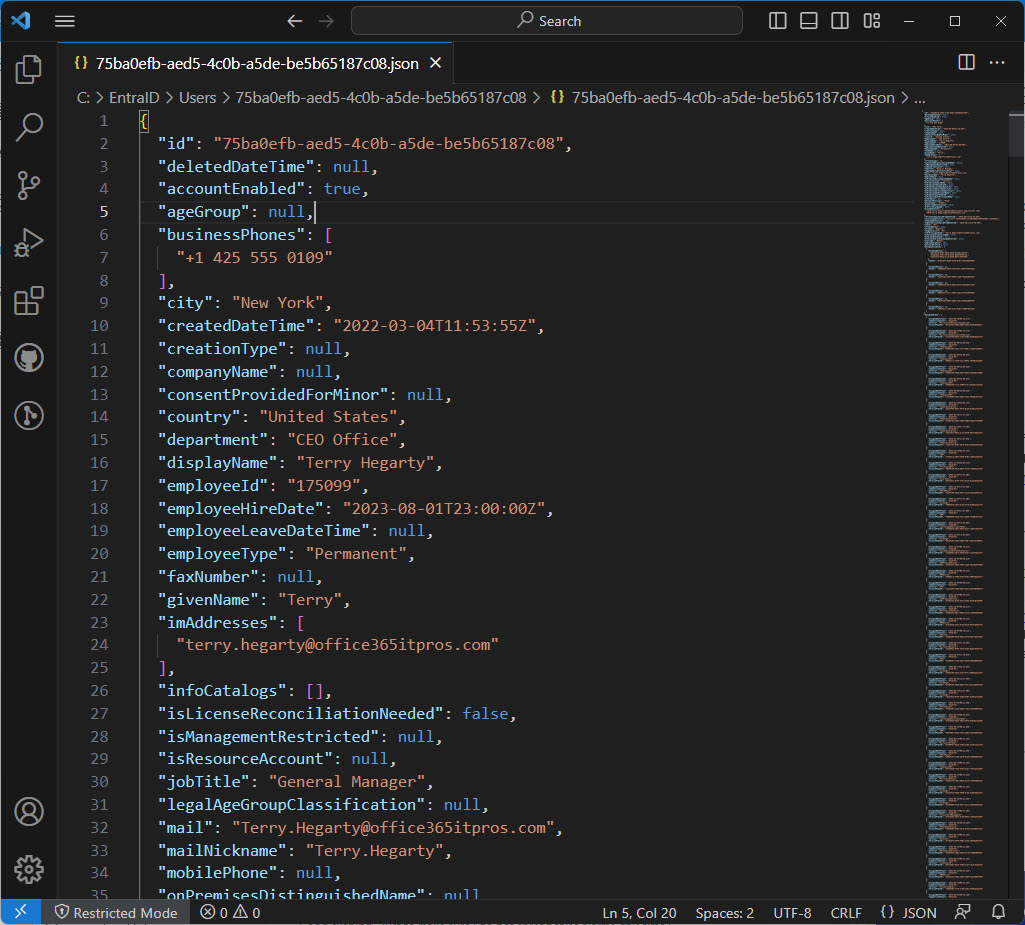
The EntraExporter toolis a PowerShell module that generates details of objects in an Entra ID tenant configuration (like groups, policies, and users) and creates JSON files. It’s a great way to capture point-in-time information about Entra ID (Azure AD) configuration. Although you can’t replay the captured data to recreate objects, having all the information available is a great start if you need to restore or replay anything.
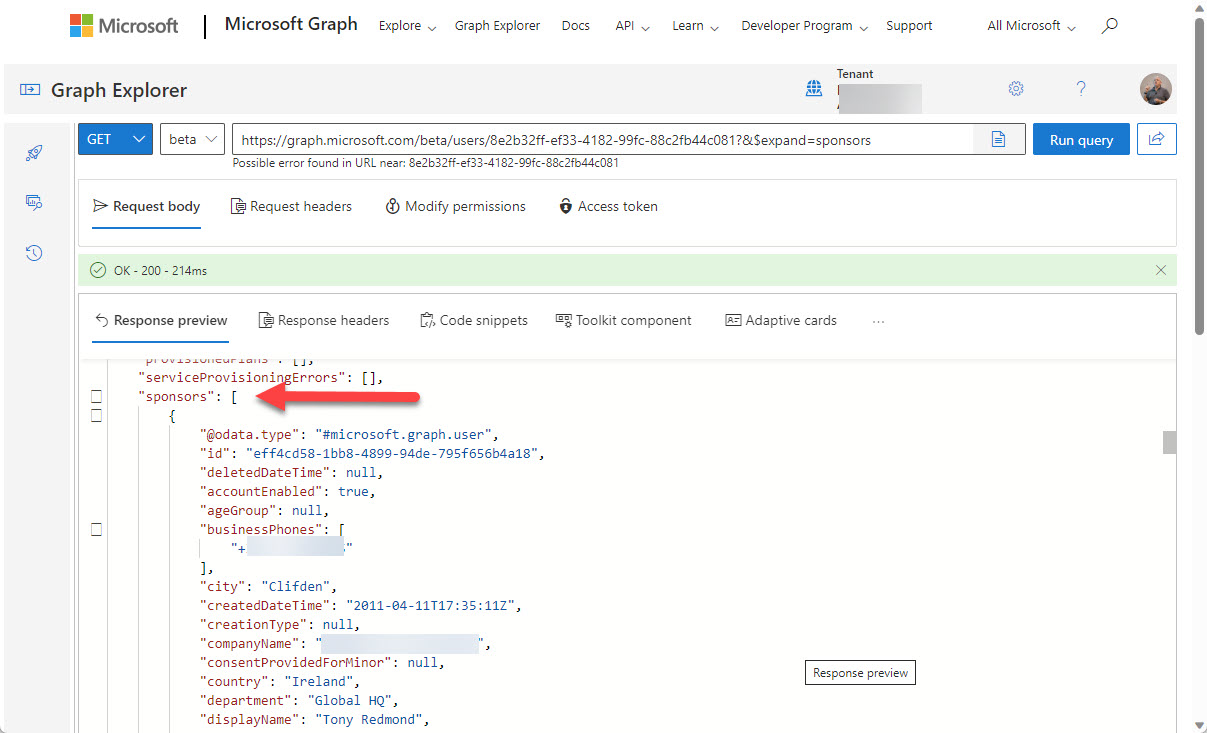
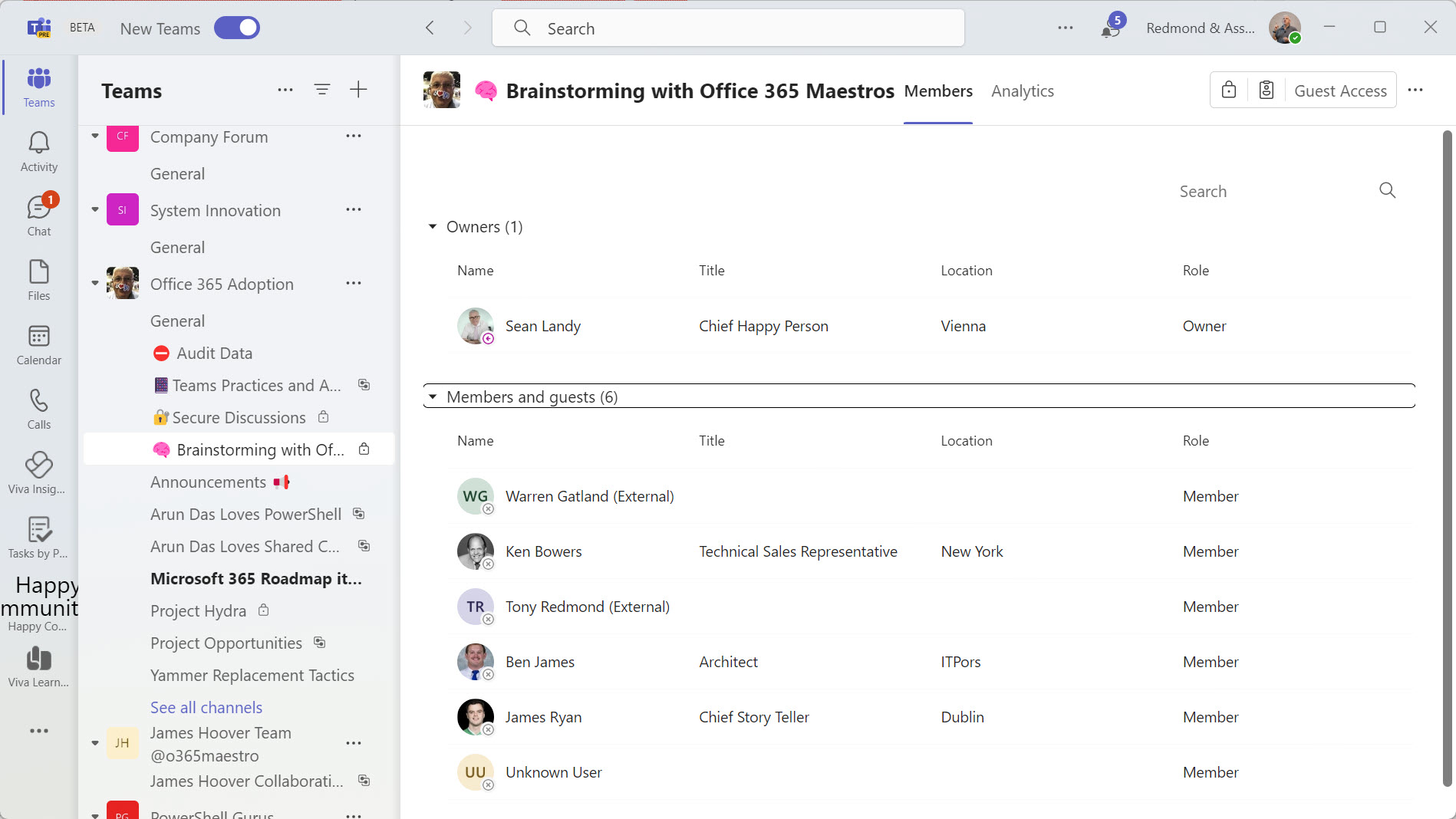
You can now define Entra ID guest account sponsors using the Entra ID admin center or PowerShell. A sponsor is an account or group that knows why a guest account exists. During operations like account reviews of the membership of a Microsoft 365 group, sponsors can help group owners decide if guest accounts should continue as members or should be removed. I’m sure others will come up with ideas for using guest account sponsors, but that’s what we have for now.
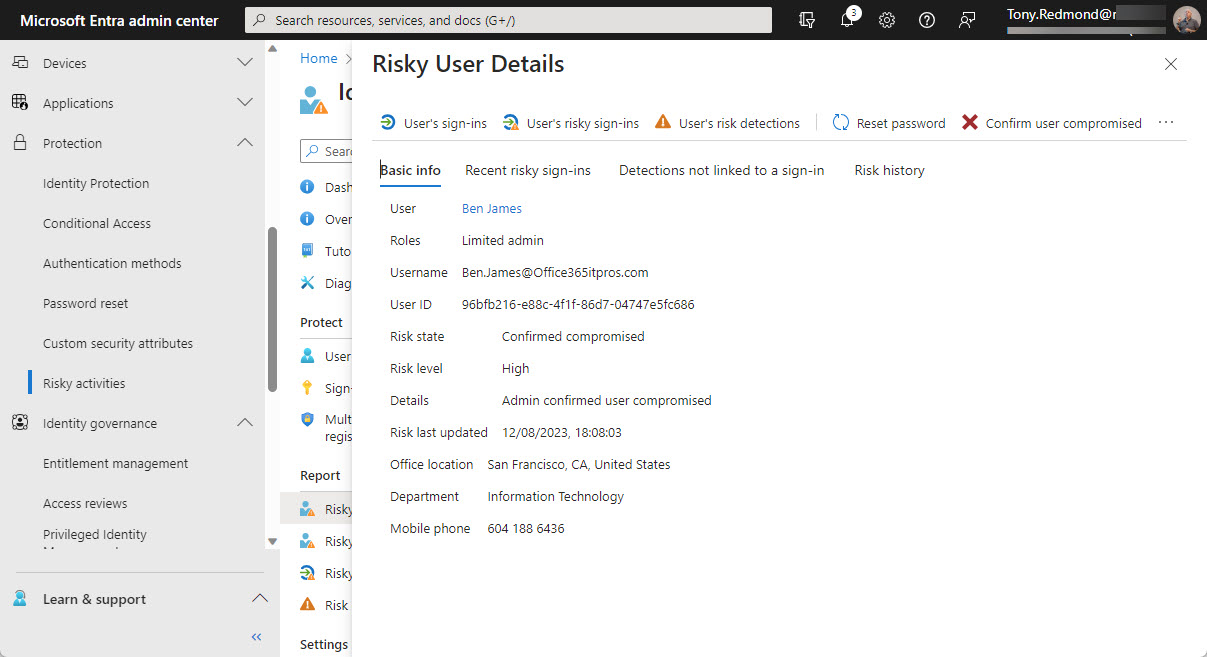
Entra ID risky users are accounts that Entra ID Identity Protection detects as exhibiting signs of suspicious activity that might mean the accounts are compromised. In this article, we consider the value of Entra ID risky accounts and how they can be used in conditional access policies. And a look at the Microsoft Graph PowerShell SDK cmdlets that are available to risky users too!
A new preview capability supports filtering against the Azure AD employee hire date property (Entra ID). Two different filter types are available to support the PowerShell ge and le operators. One filter checks against a set date, the other uses a calculated date. Both work well, and hopefully this development means that the Entra ID developers will enable the same capability for the Get-MgUser cmdlet.
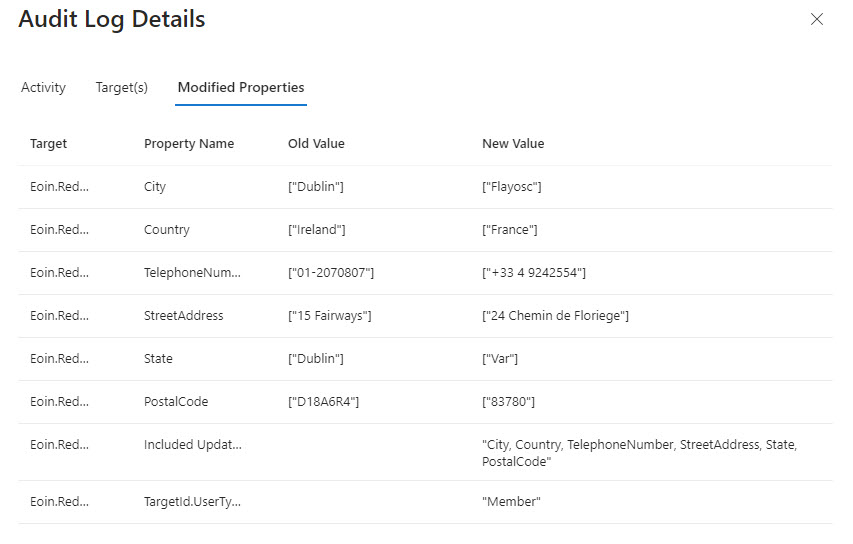
A Twitter discussion about how to audit user account changes revealed that Entra ID does not capture details of changes to the usage location for an account. The possibility existed that the data might be present in the information ingested from Entra ID into the unified audit log, but that turned out not to be the case. Even if some properties are missing, a PowerShell script demonstrates the principle of how to report user account changes (old and new properties). But it would be nice if Entra ID captured details about changes to the UsageLocation property.
A reader asked why some deleted Microsoft 365 user accounts appear to have assigned licenses. That seemed strange because licenses are freed up for reuse when accounts are deleted, so we took a look behind the scenes to find out why some deleted user accounts keep license information in their properties and some do not.
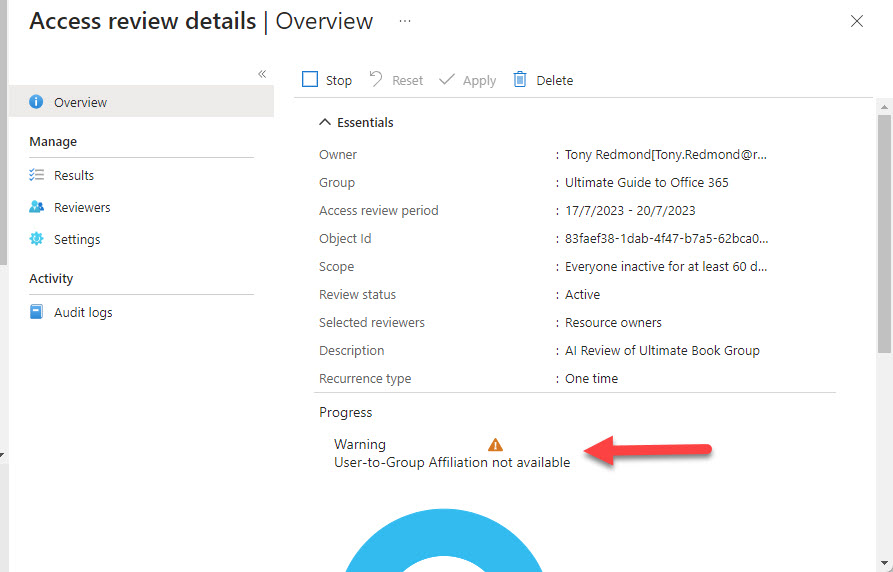
Microsoft has added a machine learning feature to Entra ID Access Reviews. The new feature checks affiliation between users and the group being reviewed. It’s an interesting idea, but only if the manager-employee relationships in your directory are accurate because that’s what Entra ID Access Reviews use to check affiliation. Microsoft Entra ID Governance licenses are needed for the new features… Another $7/user/month!
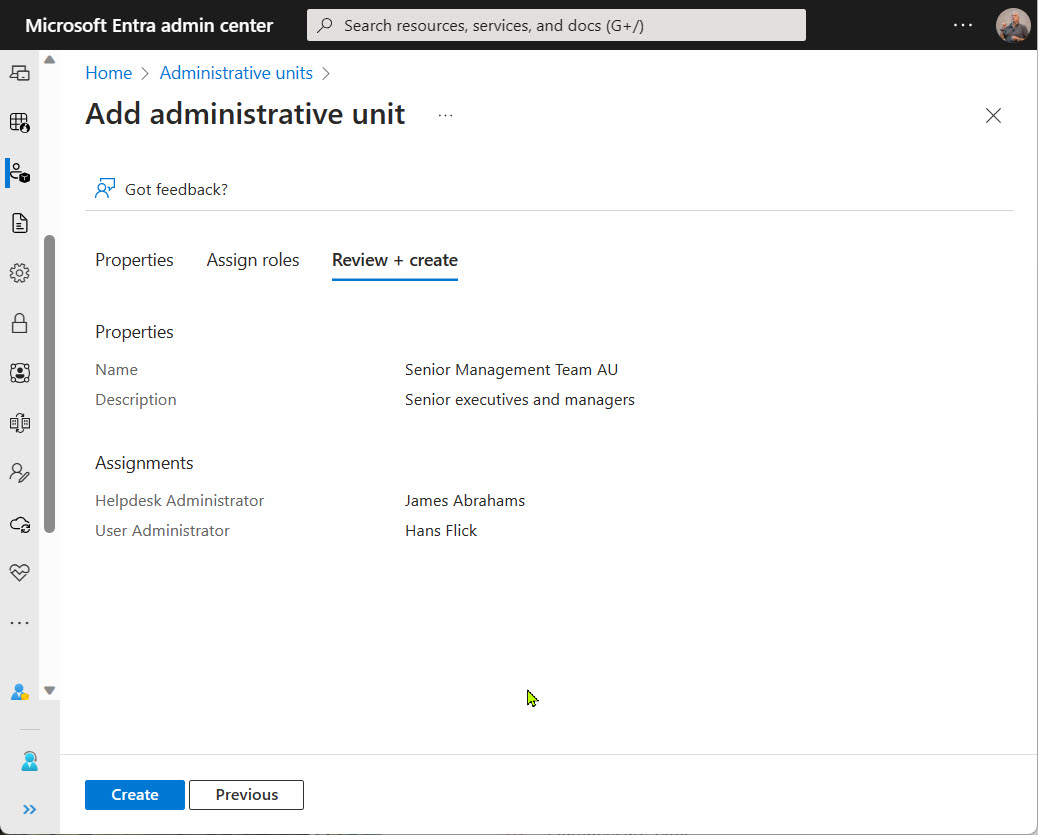
Restricted administrative units (preview) are a new mechanism to support scoped management of Entra ID user accounts, devices, and security groups. You’ll need Premium P1 licenses for the accounts assigned management roles for these AUs, but that seems like a small price to pay for the functionality.
Microsoft announced that they are rebranding Azure AD to become Microsoft Entra ID. This is just a name change and no functionality or licenses are affected. It’s simply yet another Microsoft rebranding exercise like Microsoft 365, Purview, and Defender. The name change will start in the latter half of 2023 and be completed by 2024.
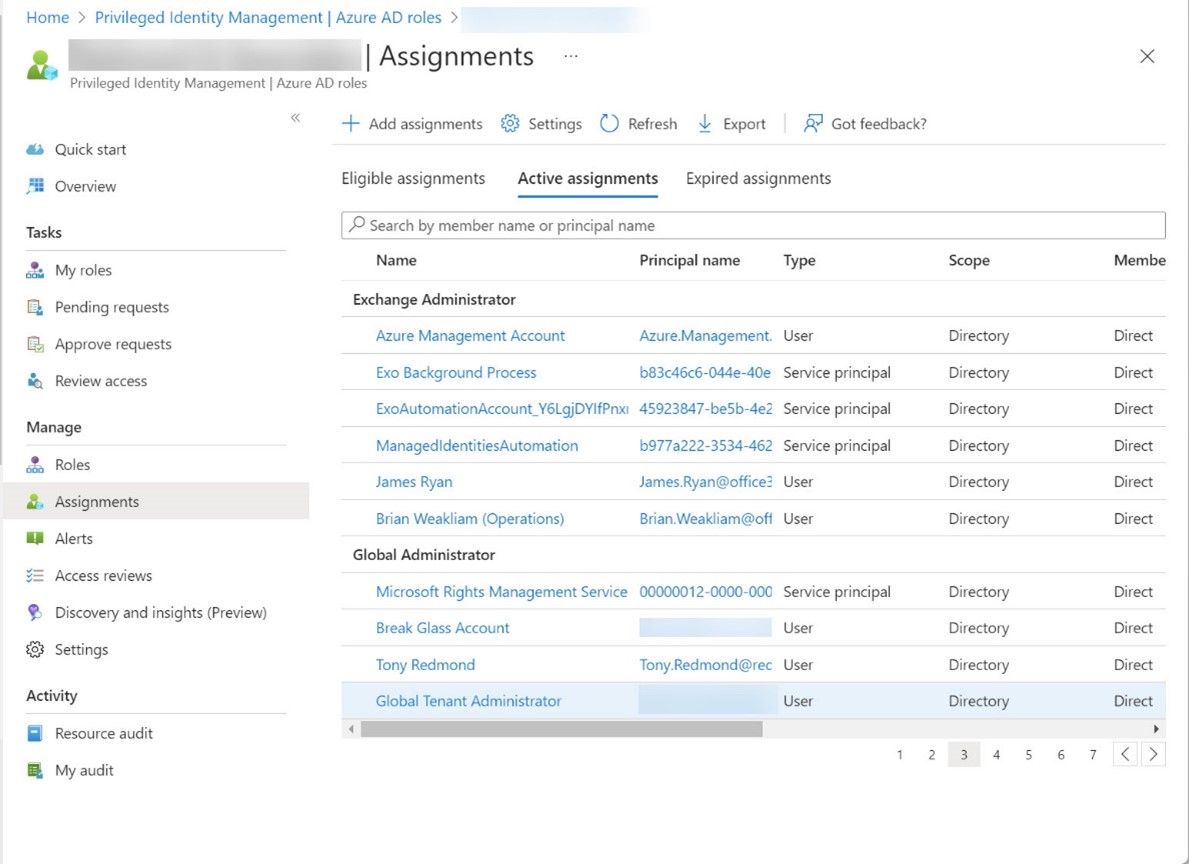
PIM, or Privileged Identity Management, is a solution for managing the assignment of privileged Entra ID roles to users and groups. PIM role assignments can be active or eligible. If you report “normal” role assignments, you only see the currently active set. Some more processing is needed to fetch the PIM assignments. Here’s our version of a script to do the job for holders of the Exchange administrator and Global administrator roles.
Up to now, the Microsoft Graph PowerShell SDK has not included a cmdlet capable of reporting the renewal dates for Microsoft 365 subscriptions. A new beta Graph subscriptions endpoint is a method to retrieve the renewal information. Even if you can’t use an off-the-shelf cmdlet, you can still get the data.
Being able to set user-preferred authentication methods for Entra ID multi-factor authentication hasn’t been possible up to now. New Graph APIs make it possible to get and set authentication methods for Entra ID accounts. It’s just another small step along the line to migrate away from the MSOL and Azure AD modules.
Sometimes, long running PowerShell scripts encounter the problem of Azure AD access token lifetime expiration. In other words, the default lifetime of tokens issued by Azure AD is too short to allow the script to complete before the token expires. Two solutions exist. Use a token lifetime policy to prolong access token lifetimes or check in code for potential expiration and renew when necessary.
I now have a Microsoft Graph Early Adopter badge. I didn’t ask for it. The badge just arrived via email. Which brings me to how to deliver product feedback. Sure, you can make comments via GitHub, but that ignores a perfectly good feedback portal developed to allow people to give direct feedback (including requests for new features) to Microsoft. You won’t get a badge for providing feedback via the portal, but it’s the right thing to do.
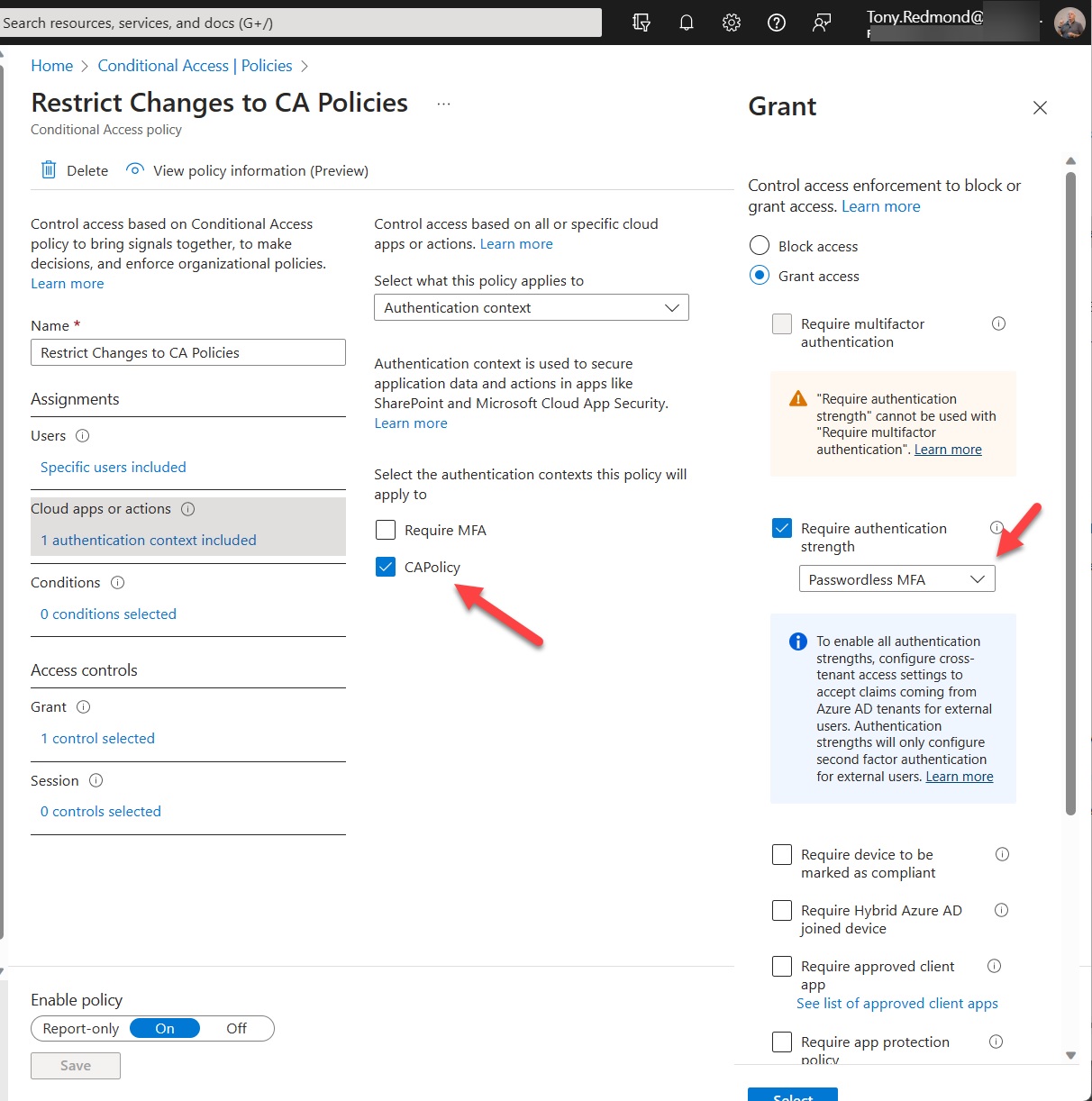
Protected actions are a new preview feature for Azure AD conditional access policies. You can associate protected actions with an authentication context and specify that anyone who wants to use these actions should meet the conditions set in a conditional access policy. Although only a limited set of actions are available in the preview, you can see the value of what Microsoft is doing and how it might apply to actions across the Entra and Azure portals.
Teams Shared Channels are a great way to collaborate across multiple Microsoft 365 tenants. From an administrative side, it’s nice to know about who’s connecting – who’s coming into your tenant to use a Teams shared channel and who’s leaving your tenant to share ideas in a Teams shared channel belonging to another tenant. This article explains how to retrieve that information from Azure AD shared user profiles.