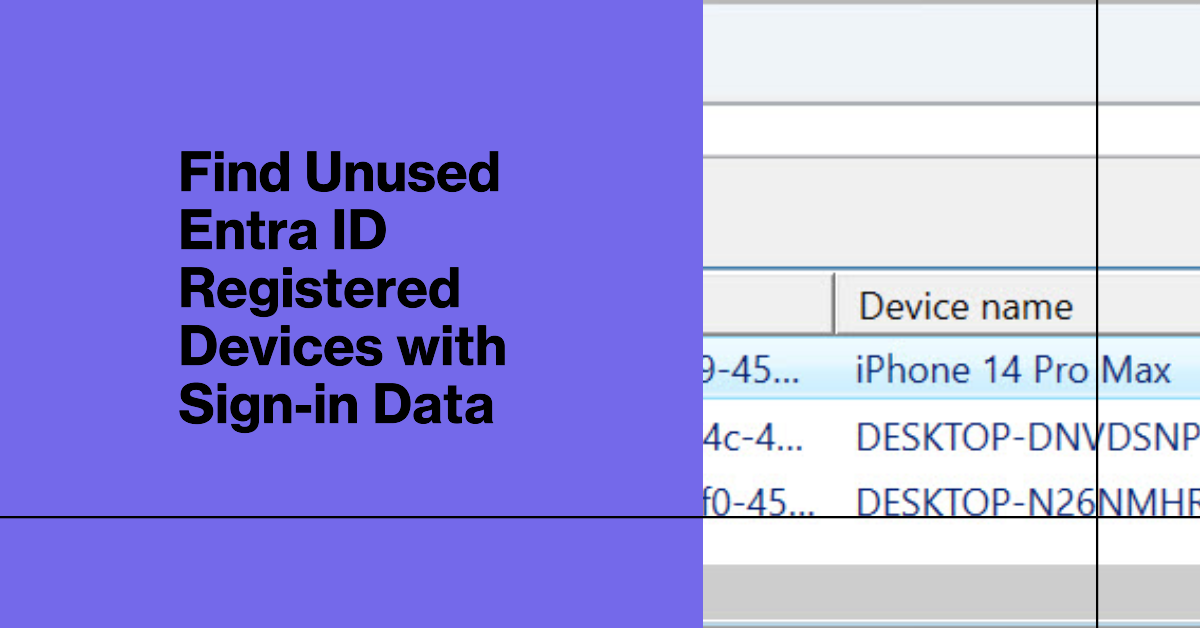
This article describes how to use sign-in data to identify unused Entra ID registered devices. It’s an imperfect solution because Entra ID doesn’t log device information in many sign-in records. I’m sure there’s a good reason why Microsoft doesn’t capture the device information, but it’s a little frustrating. We have an imperfect and partial solution, but that’s better than nothing.
A Microsoft Technical Community article gave some interesting information about how to report soft-deleted Entra ID objects. We think we can improve the information by tweaking the script, especially to include the object type in the output. As always, you can download the script from GitHub.
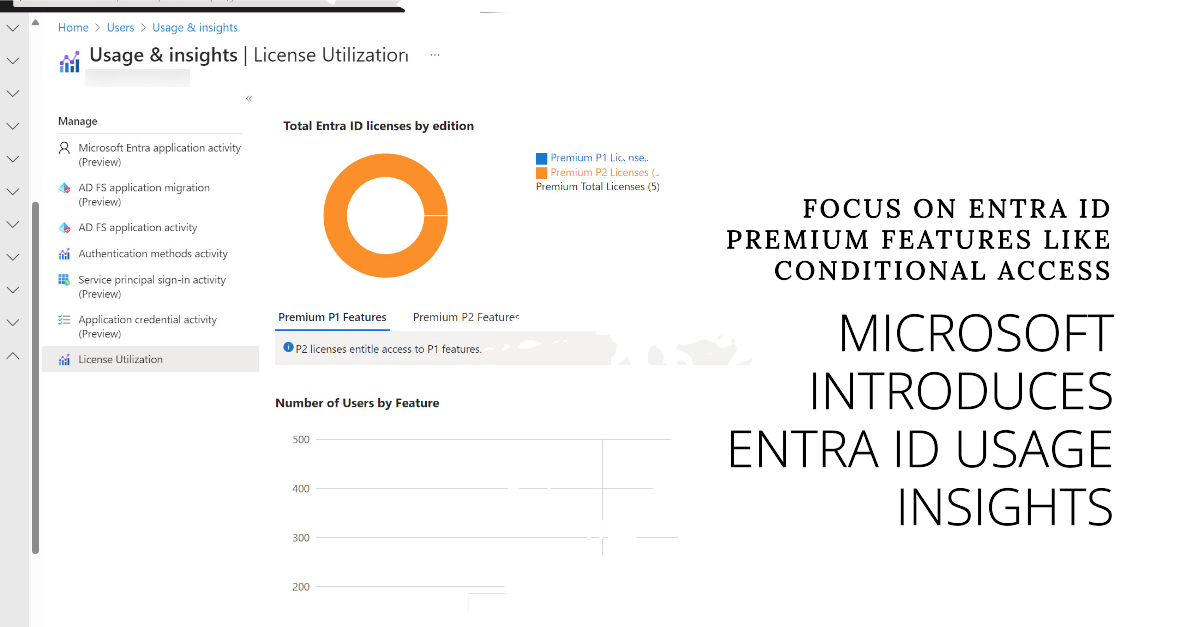
Microsoft has released the preview of the Entra ID usage insights for premium license consumption. This could be the harbinger of a more restricted licensing regime for Entra ID premium features such as conditional access. Putting any barrier in place to stop more accounts being protected by multifactor authentication seems like a bad idea. Let’s hope that this isn’t the case here.
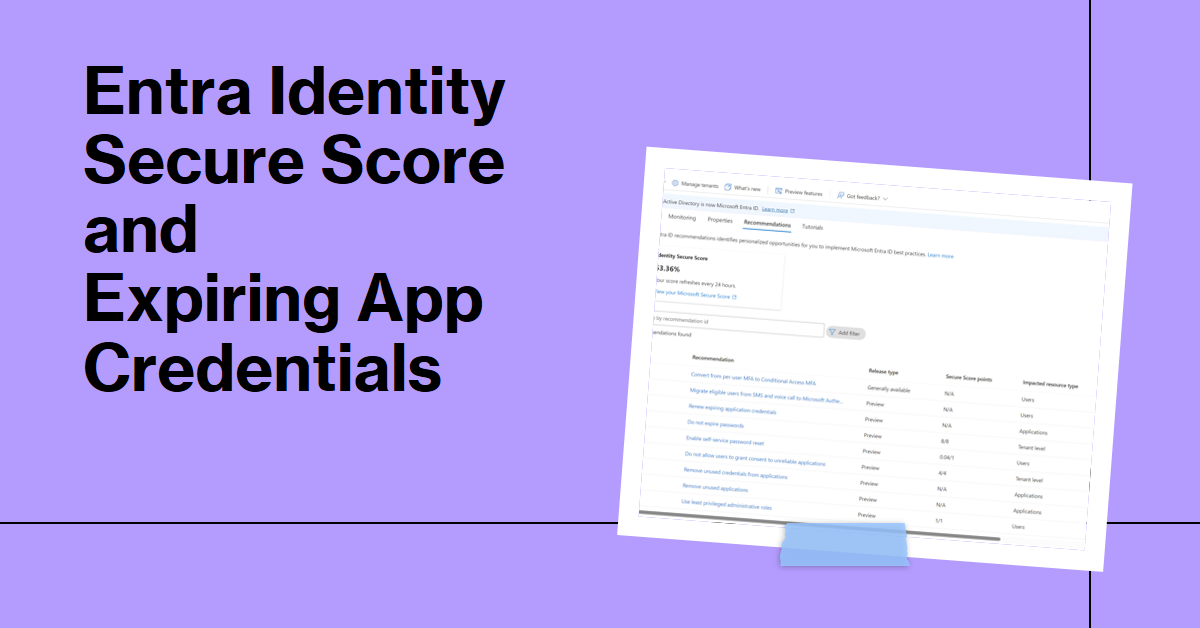
If your Microsoft 365 tenant has Entra P2 licenses, you can use the Entra Identity Secure Score feature to measure your tenant against Microsoft benchmarks and recommendations, including expiring app credentials. The fact that credentials expire is one of the reasons why I don’t use apps as much any more. Using the Microsoft Graph PowerShell SDK is just easier.
If conditional access policies impose MFA for all cloud apps, it gives external users a problem when they use Outlook desktop to read protected email. The issue is because Outlook can’t obtain a use license to decrypt the content because it can’t satisfy the MFA challenge. It’s an example of how two good parts of the Microsoft 365 ecosystem clash.
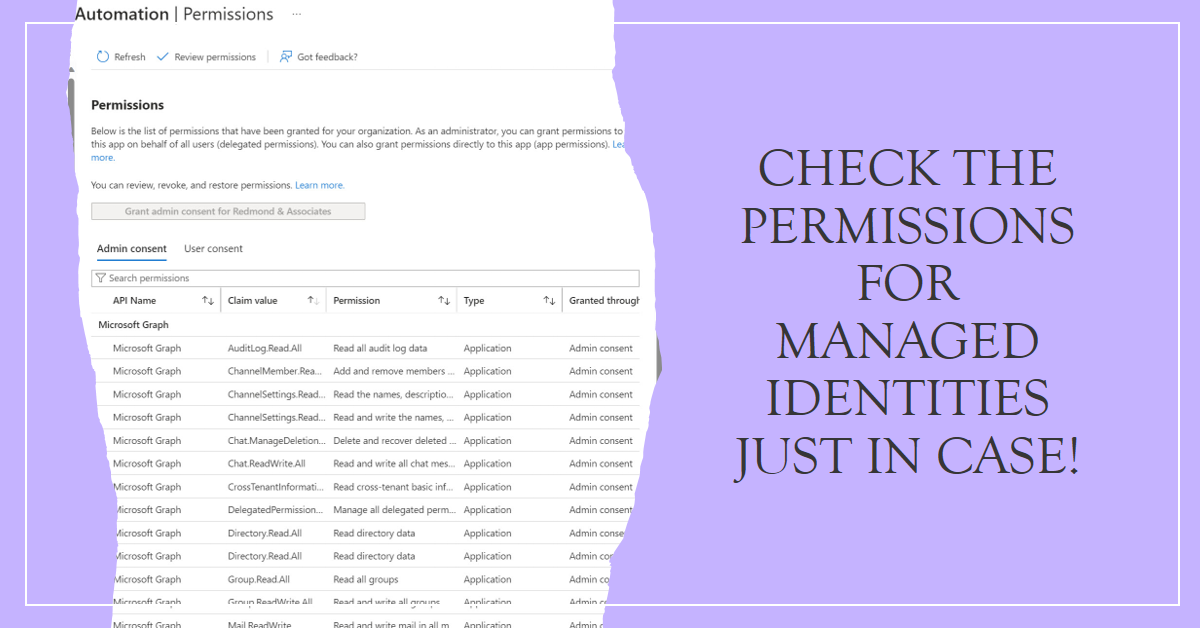
This article explains how to check Managed Identity permissions, or rather the set of consented Graph and other permissions held by the service principals used for managed identities. These can become highly permissioned over time, and that’s why checking periodically is a good idea.
The latest version of the MSIndentityTools PowerShell module includes the Export-MsIdAppConsentGrantReport cmdlet to generate a report of OAuth app permissions. Allied with the ImportExcel module, the cmdlet can produce a very nice workbook containing lots of information about permissions held by the apps in a tenant. But even better, you can export the data to PowerShell and use it in your scripts.
The Graph User.ReadBasic.All permission is now available for both delegated and application usage. Think before rushing to use the permission. Although the permission does what it sets out to do, the restriction on filtering means that many scenarios need the full User.Read.All permission.
Microsoft is changing the way that Exchange Online address book updates work to force users to use search rather than browsing through the GAL/OAB. That’s fine and should improve things. When playing with finding how many items are in the GAL, I found that the Get-MgDomainNameReference cmdlet appears to have some issues. First, it can only return up to 999 items, which isn’t a lot when you’re dealing with users and groups that have a connection to a domain. Second, it doesn’t return a nextlink, so you can never fetch all available items. It just goes to prove that Microsoft Graph PowerShell SDK cmdlets are at the mercy of the underlying APIs.
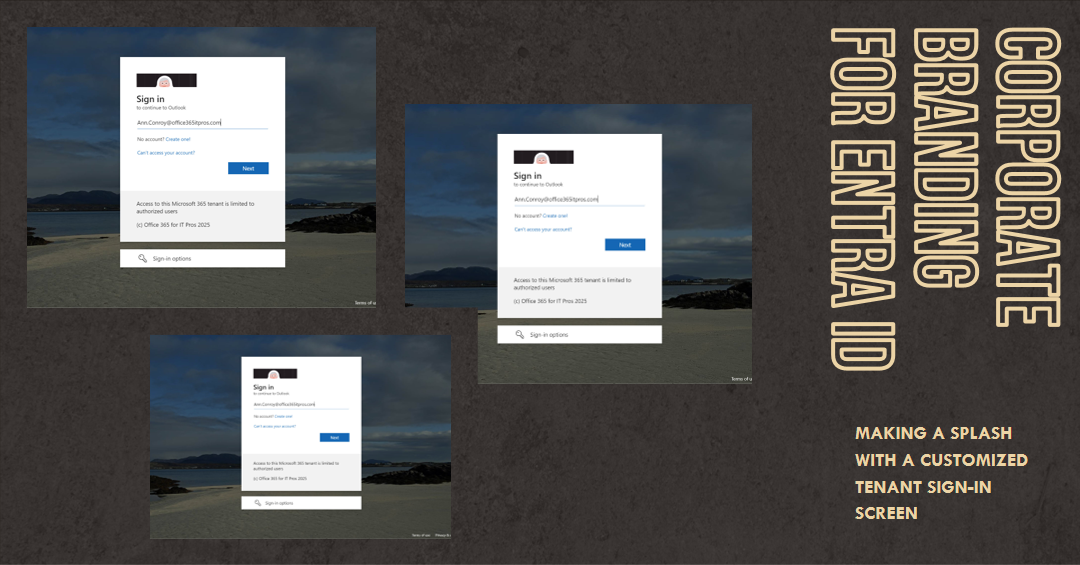
The ability to apply custom corporate branding for Entra Id screens has existed since 2020. You can update elements through the admin center or PowerShell. This article explains how to use the Microsoft Graph PowerShell SDK to customize the sign-in text and background image for the sign-in screen.
MC705357 (9 Jan 2024) says that the dynamic group rule builder in the Entra ID and Intune admin centers no longer supports the contains and notContains operators. There’s no real cause to worry because existing rules continue to work and if you need to use contains or notContains in a membership rule, you can edit the rule manually.
Entra ID registered apps can authenticate using app secrets and certificates. These credentials expire over time, so it’s good to review app credential expiration dates periodically. This article explains how to use the Microsoft Graph PowerShell SDK to generate a report about app credential expiration dates to allow tenant administrators to manage registered apps a little better…
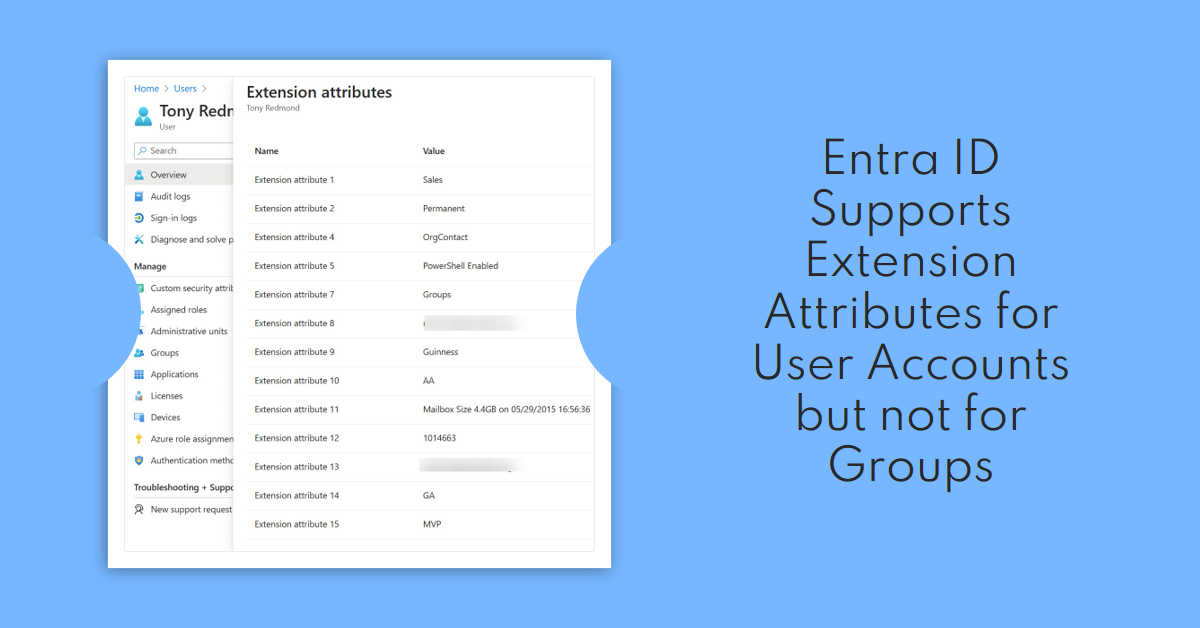
Entra ID supports user extension attributes but the same facility is unavailable for group objects. That seems strange, but it might be due to the way that Entra ID thinks about group object. In any case, it’s an inconsistency that Microsoft should address. Also covered is how to report problems with Graph SDK cmdlets and a new function to help you understand the permissions needed to run a script.
Password profiles store the password settings for Entra ID user accounts. By updating the password profile, you can update an account’s password and force actions like force the user to change their password on the next sign-in or force the user to enable multifactor authentication for the account. All done with cmdlets from the Microsoft Graph PowerShell SDK.
A question came in about how to report admin consent requests as viewed through the Entra ID admin center. PowerShell does the trick, once you know how. The key thing is to find the right cmdlet to use. Once you know that, the rest is pretty easy as we explain in this article.
OAuth apps are a big part of the extensibility picture for Microsoft 365 tenants. As such, they are targeted by attackers as a good way to gain access to data. In a recent security blog, Microsoft recommends some steps to secure tenants. We’ve covered most of them in other articles, but it’s always good to pull the story together and rewrite a script to make it easier to report consent grants for apps.
The preview app instance property lock feature designed to improve the security of Entra ID registered apps is becoming the default for new apps. In this article, we describe how to update the app instance property lock to reflect the new default setting using cmdlets from the Microsoft Graph PowerShell SDK, including a script you can download and run.
Entra ID captures the lastSuccessfulSignInDateTime property to record the last successful sign-in action against user accounts. The new property is available through the Graph beta endpoint. Quite a difference can exist between the last successful sign in and the last sign in, as explored in this article.
Conditional access policies control access to Entra ID connections. Policies should have exclusions for breakglass accounts, but sometimes this doesn’t happen. This article explains how to use cmdlets from the Microsoft Graph PowerShell SDK to check conditional access policies and update policies with exclusions where necessary.
A year ago, I wrote about the ability to pause membership processing for dynamic Entra ID groups. Now we return to consider the reasons for pausing processing. Mostly suitable circumstances occur when the directory is in a state of flux, often caused by corporate restructuring or similar scenarios. When this happens, you can pause processing for all dynamic groups and restart once the directory stabilizes.
A reader asked how to report user and group assignments for enterprise apps. As it turns out, this isn’t particularly difficult, if you know where to look. Our script uses the Graph SDK to check service principals, filters out the apps to check, and extracts the user and group assignments before reporting what it finds.
On November 6, Microsoft announced that they will deploy Microsoft-managed conditional access policies to eligible tenants. A conditional access policy controls the connections users want to make to apps or data by setting conditions. In this case, the Microsoft policies will require MFA before access is granted to apps like administrative portals.
The question of how best to block PowerShell access for Microsoft 365 user accounts deserved some consideration. The answer lies in service principals for the enterprise accounts created by Microsoft to allow PowerShell modules to authenticate with Entra ID. By restricting access to an assigned security group, you effectively block access to anyone outside that group.
This article explains how to use PowerShell to remove licenses from disabled accounts, including some caveats such as not removing Exchange Online licenses. Organizations might want to do this to save money on Microsoft 365 license fees while an account is temporarily unused. Removal of Exchange Online licenses can result in the loss of a mailbox, and you don’t want that to happen if you’re disabling accounts just because someone is on a long-term sabbatical or other leave of absence.
This article explains how to use PowerShell to create dynamic Microsoft 365 groups (and teams) based on the departments assigned to Entra ID user accounts. Creating a new group is easy. The trick in team-enablement is to wait for the synchronization between Entra ID and Teams to finish before you go ahead. After that, it’s plain sailing.
A reader asked how they could create dynamic administrative units for every department in their directory. A PowerShell script does the job, even if some constraints in how Entra ID processes membership rules means that the rules can’t be quite as precise as I would like them to be.
Entra ID includes a registration campaign feature to help organizations move users to stronger authentication methods like the Authenticator app. Running campaigns is a good thing, unless you decide to do it when the administrators are away from the office (like me) or users are unprepared. But it is time to get rid of SMS and voice responses to MFA challenges, so maybe you should schedule a campaign soon?
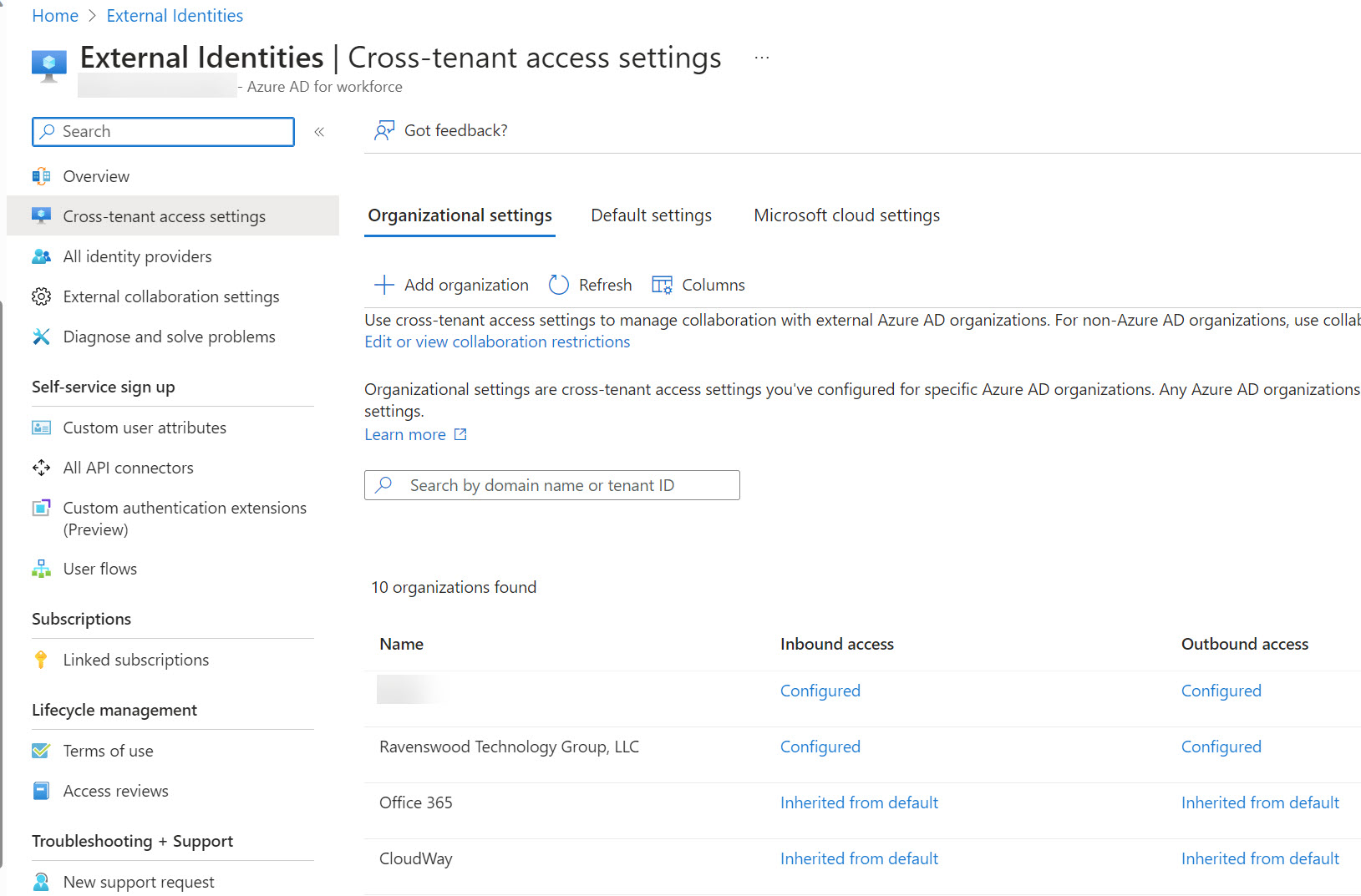
Microsoft announced three changes to Entra ID cross-tenant access settings that will improve how the settings work for large enterprise tenants in particular. One of the changes improves the blocking of Entra ID B2B Collaboration invitations extended to allow guest users access resources in a tenant. When Entra ID evaluates whether it should issue an invitation, it now takes the blocklist (if set) in the B2B collaboration policy and cross-tenant access settings into account. It’s the way things should have worked from the start.
The EntraExporter toolis a PowerShell module that generates details of objects in an Entra ID tenant configuration (like groups, policies, and users) and creates JSON files. It’s a great way to capture point-in-time information about Entra ID (Azure AD) configuration. Although you can’t replay the captured data to recreate objects, having all the information available is a great start if you need to restore or replay anything.
A question about how to report specific changes to Teams memberships gave another excuse to use PowerShell with the unified audit log to deliver a solution. The idea is that you can check audit log entries to see when specific user accounts join the membership of Teams. Once you’ve found that data, it’s a simple matter of creating email to share the results. All done with a few lines of PowerShell…
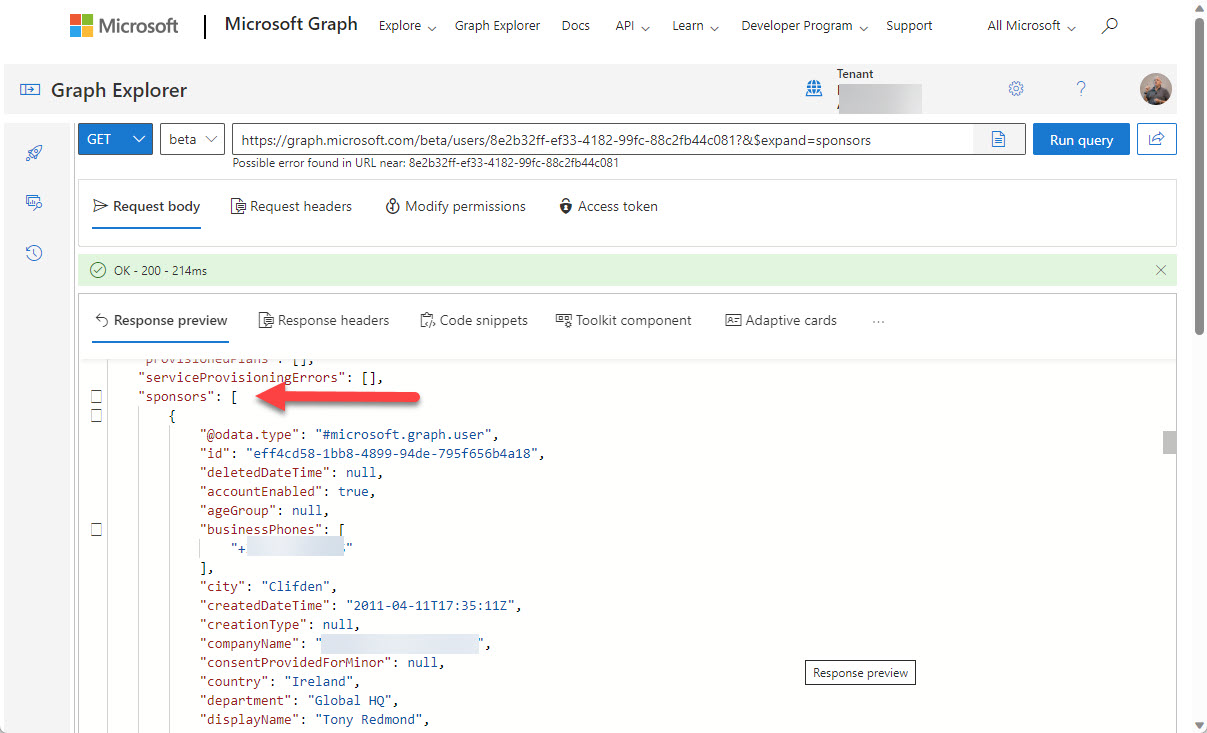
You can now define Entra ID guest account sponsors using the Entra ID admin center or PowerShell. A sponsor is an account or group that knows why a guest account exists. During operations like account reviews of the membership of a Microsoft 365 group, sponsors can help group owners decide if guest accounts should continue as members or should be removed. I’m sure others will come up with ideas for using guest account sponsors, but that’s what we have for now.
Entra ID risky users are accounts that Entra ID Identity Protection detects as exhibiting signs of suspicious activity that might mean the accounts are compromised. In this article, we consider the value of Entra ID risky accounts and how they can be used in conditional access policies. And a look at the Microsoft Graph PowerShell SDK cmdlets that are available to risky users too!
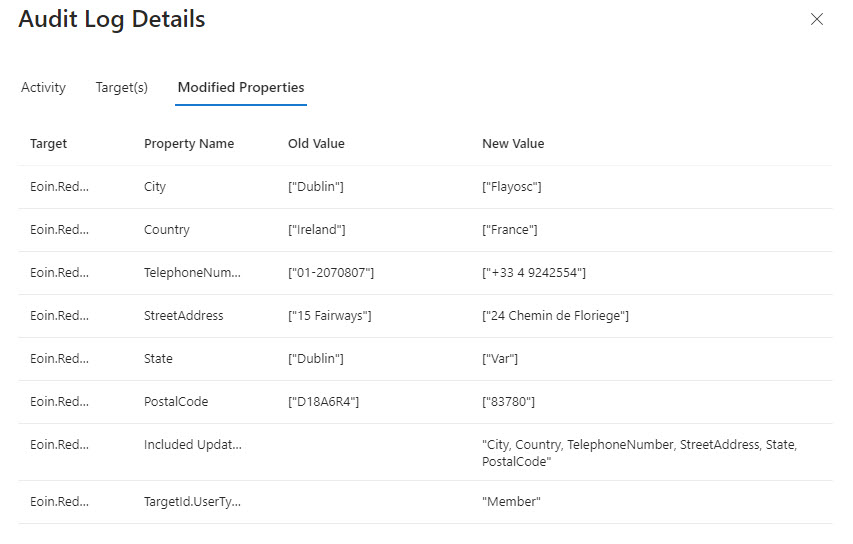
A Twitter discussion about how to audit user account changes revealed that Entra ID does not capture details of changes to the usage location for an account. The possibility existed that the data might be present in the information ingested from Entra ID into the unified audit log, but that turned out not to be the case. Even if some properties are missing, a PowerShell script demonstrates the principle of how to report user account changes (old and new properties). But it would be nice if Entra ID captured details about changes to the UsageLocation property.
A reader asked why some deleted Microsoft 365 user accounts appear to have assigned licenses. That seemed strange because licenses are freed up for reuse when accounts are deleted, so we took a look behind the scenes to find out why some deleted user accounts keep license information in their properties and some do not.
Token protection is a new session control (preview) for Entra ID conditional access policies. The idea is to bind a sign-in token to a user’s device to stop attackers attempting to reuse the token to compromise the user’s account. Only a limited set of Microsoft 365 apps support token protection at present, but it’s an idea that should help if token theft becomes as pervasive as some predict.
Two years ago, I wrote about how to generate a report about managers and the direct report from the information stored in Entra ID. As it turns out, the Get-User and Get-Recipient cmdlets have a little flaw that can make the data they return inaccurate. To make sure that the data is correct, a new version of the script uses cmdlets from the Microsoft Graph PowerShell SDK to report Entra ID managers and reports. We also format the output in a nicer way, so it’s all good.
The AzureAD PowerShell retirement date is approaching quickly. After March 30, 2023, Microsoft says that the module will work for six months. Then? Who knows!. Cmdlets that set licenses for Azure AD accounts are now retired and will stop working on or before March 30, 2024. If you haven’t already upgraded scripts, it’s time to do so.
The first app in a new community project called IdPowerToys helps Microsoft 365 tenants to document conditional access policy settings in PowerPoint. The information used to document the CA policies is extracted (manually or automatically) from Azure AD, analyzed, and output as a PowerPoint presentation. It’s a nice way to see what CA policies exist in a Microsoft 365 tenant and helpful if you want to rationalize the set of policies in use.
It’s easy to invite people to become guest users in a Microsoft 365 tenant, but some of the invitees never accept the invitation. Perhaps they don’t need to redeem the invitation to do work or maybe it’s because they don’t want to. In either case, Entra ID guest accounts with unredeemed invitations can accumulate and become stale. In this post, we discuss how to use PowerShell to find and remove those stale accounts in a safe manner.
Entra ID registered devices store some information about the operating system and version used when registration occurs. Although this information changes over time and isn’t updated by Azure AD, it might be of some interest and use to tenant administrators, so we show how to report it here. If you want accurate information, you’ll need to use Intune.